“May contain nuts!”…….. In an email world of attachments, remain detached.
Apologies if I am beginning to sound like a broken record but I find myself, once again, writing a short piece on bogus emails and the dangers that lie within. It’s too big and common a problem to ignore.
Below is an image of an email I have seen today.
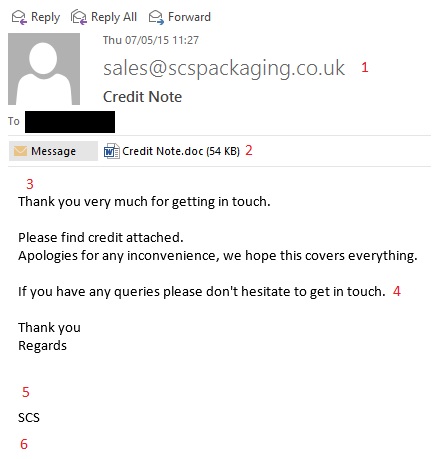
1 – nothing too suspicious about the purported sender address format – but is this a company with whom you trade and are you expecting a credit note?
2 – the message contains an attachment which should instantly trigger a higher degree of care from us as recipients and users – start to look more closely
3 – no personalised salutation where one might have expected a “Dear John” or “Hi Fred” as appropriate for the intended recipient – a cause for suspicion
4 – the sender invites the recipient to get in touch with any queries without leaving any useful contact details – odd, don’t you think?
5 – no personalised sign off, just the generic initials of the purported company – further cause for suspicion
6 – no trace of a signature where one might expect some level of contact details given the invitation to contact with queries – with the accumulated observations noted, think hard!
Alarm bells should be ringing by now, overriding any thought that the only way to get to the bottom of this is to open the attachment. Step back and with a cool head think through;
– Do you deal with the purported company?
– Even if you do, does this match the correspondence you normally receive
– Have you asked them for a credit note?
If you really think there is an outside chance of the validity of the communication, contact the company directly and ask the question. Remember, it is much better to take a few minutes investigating the correspondence than the quick click which might create a much bigger problem for yourself or your entire network.
Don’t rely on mail filtering and antivirus tools to do the sceptical analysis for you. If the weakest link in the defence line is the user’s curiosity, that is where the malicious code writer will focus his attention. A recent BBC article from 5th May reminds us that infection often takes place, “….after a booby-trapped attachment on a phishing message had been opened”.
For more information, see http://www.bbc.co.uk/news/technology-32591265
(The article discusses a new virus which attempts to steal data but which can also render the computer unusable to avoid detection and analysis).
If in doubt, give us a call on 0118 976 7111 and let us help you assess the risk and act accordingly – we’re here to help and ensure you get it right…..from the start.
Part of the “May contain nuts” series of short articles discussing familiar topics which we should all revisit once in a while.
