Beyond MFA – Keeping your accounts secure
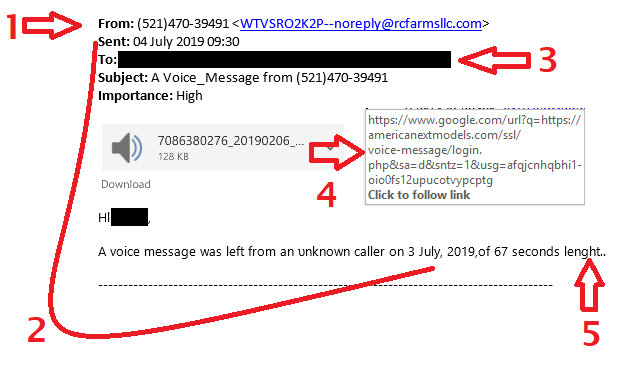
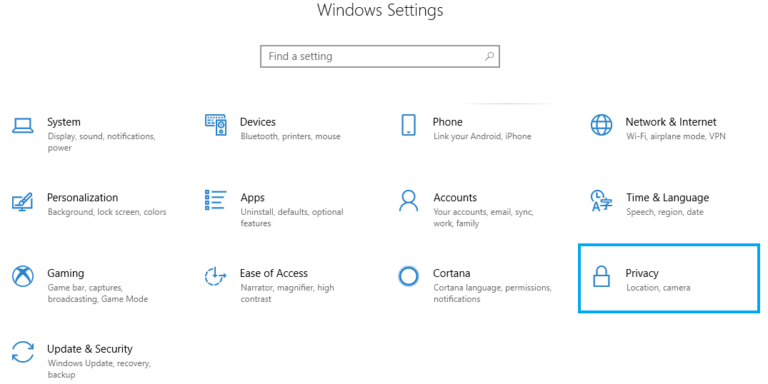
Multi-Factor Authentication (MFA) and Two-Factor Authentication (2FA) have both become key tools helping protect us from cyber threats. Requiring two or more verification steps to access an account adds a strong layer of security beyond just a password. However, even with its strengths, MFA and 2FA can still be vulnerable, especially when users approve sign-in…