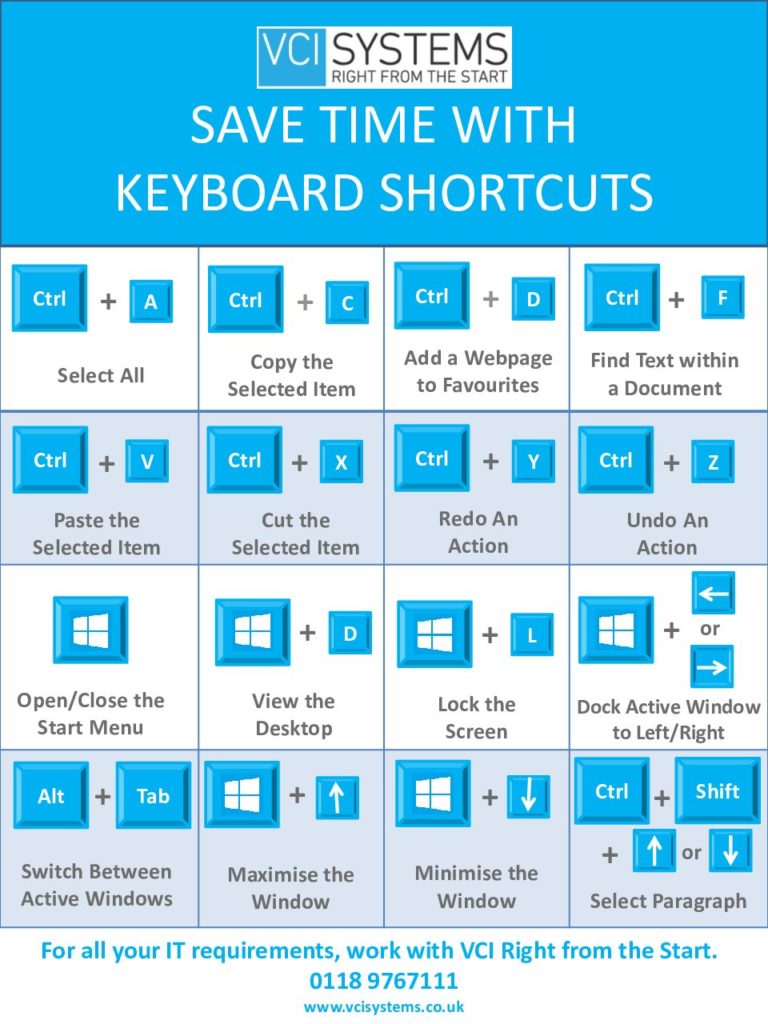
Get the most from your online meeting solution
How many people were familiar with Teams or Zoom before 2020? As the world changed dramatically in late March 2020, a significant portion of our communications and meetings suddenly shifted to a completely digital format, overtaking traditional phone calls and conference calls. The convenience of the format has lasted well beyond the lock-down years. Although…